Local Group Policy Editor is a Microsoft Management Console (MMC) snap-in that you can use to edit local Group Policy objects (GPOs). Local Group Policy Editor and the Resultant Set of Policy snap-in are available in Windows Server 2008 R2 and Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise. Group Policy Editor (gpedit) is a Windows built-in tool that facilitates an interface for administrators to configure computer and user settings related to Windows and installed software.Certain. Jul 08, 2011 If you try to open the Group Policy Editor in Windows 7 Home Premium, Starter or Basic by typing gpedit.msc in the start menu search box or try to run it, the “local Group Policy Editor” window will open with the following message, “MMC could not create the snap-in”. A Microsoft Management Console (MMC)-based tool that manages both computer and user-related configurations for an individual computer policy. This tool is included with Windows® 7 Service Pack 1 (SP1) and Windows 8.1. Here's a list of the policy settings you can use, based on the configuration type. For more info, see Local Group Policy Editor. Local Group Policy Editor.; 2 minutes to read; In this article Applies To: Windows Server 2012 R2. Local Group Policy Editor is a Microsoft Management Console (MMC) snap-in that is used to configure and modify Group Policy settings within Group Policy Objects (GPOs).
The Group Policy Editor is a Windows administration tool that allows users to configure many important settings on their computers or networks. Administrators can configure password requirements, startup programs, and define what applications or settings other users can change on their own. This blog will deal mostly with the Windows 10 version of Group Policy Editor (gpedit), but you can find it in Windows 7, 8, and Windows Server 2003 and later.
5 Ways to Access Local Group Policy Editor
There are plenty of different ways to get to the Local Group Policy Editor. You can find one that you are most comfortable with.
Get the Free Pen Testing Active Directory Environments EBook
Open Local Group Policy Editor in Run
- Open Search in the Toolbar and type Run, or select Run from your Start Menu.
- Type ‘gpedit.msc’ in the Run command and click OK.
Open Local Group Policy Editor in Search
- Open Search on the Toolbar
- Type ‘gpedit’ and click ‘Edit Group Policy.’
Open Local Group Policy Editor in Command Prompt
- From the Command Prompt, type ‘gpedit.msc’ and hit ‘Enter.’
Open Local Group Policy Editor in PowerShell
- In PowerShell, type ‘gpedit’ and then ‘Enter.’
If you would prefer you can also use PowerShell to make changes to Local GPOs without the UI.
Open Local Group Policy Editor in Start Menu Control Panel
- Open the Control Panel on the Start Menu.
- Click the Windows icon on the Toolbar, and then click the widget icon for Settings.
- Start typing ‘group policy’ or ‘gpedit’ and click the option to ‘Edit Group Policy.
Components of the Local Group Policy Editor
Now that you have gpedit up and running, there are a few important details to know about before you start making changes. Group policies are hierarchical, meaning that a higher-level group policy – like a domain level Group Policy – can override local policies.
Group policies are processed in the same order for each login – Local policies first, then Site level, then Domain, then Organizational Unit (OU). OU policies will override all others, and so on down the chain.

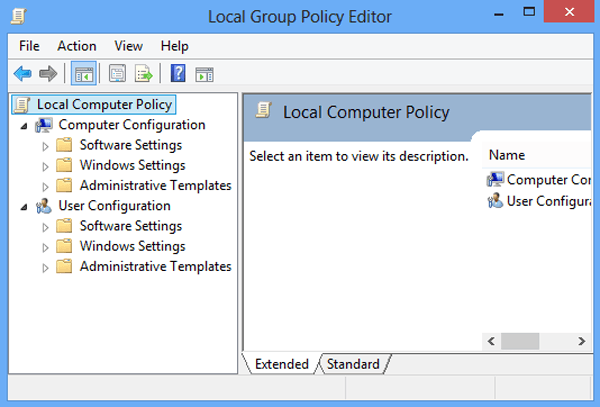
There are two major categories of group policies – Computer and User – that are in the left pane of the gpedit window.
Computer Configuration: These policies apply to the local computer, and do not change per user.
User Configuration: These policies apply to users on the local machine, and will apply to any new users in the future, on this local computer.
Those two main categories are further broken down into sub-categories:
Software Settings: Software settings contain software specific group policies: this setting is empty by default.
Window Settings: Windows settings contain local security settings. You can also set login or administrative scripts to execute changes in this category.
Administrative Templates: Administrative templates can control how the local computer behaves in many ways. These policies can change how the Control Panel looks, what printers are accessible, what options are available in the start menu, and much more.
What Can You Do With Group Policy Editor
A better question would be what can’t you do with gpedit! You can do anything from set a desktop wallpaper to disable services and remove Explorer from the default start menu. Group policies control what version of network protocols are available and enforce password rules. A corporate IT security team benefits greatly by setting up and maintaining a strict Group Policy. Here are a few examples of good IT security group policies:
- Disable removable devices like USB drives.
- Disable TLS 1.0 to enforce usage of more secure protocols.
- Limit the settings a user can change using Control Panel. Let them change screen resolution, but not the VPN settings.
- Specify a good company sanctioned wallpaper, and turn off the user’s ability to change it.
- Keep users from accessing gpedit to change any of the above settings.
That is just a few examples of how an IT security team could use Group Policies. If the IT team sets those policies at the OU or domain level, the users will not be able to change them without administrator approval them.
How to Configure a Security Policy Setting Using the Local Group Policy Editor Console
Once you have an idea of what you GPOs you want to set, using gpedit to make the changes is pretty simple.
Let’s look at a quick password setting we can change:
1. In gpedit, click Windows Settings, then Account Settings, then Password Policy.2. Select the option for “Password must meet complexity requirements.”3. If you have Administrative rights to change this setting, you could click the button next to “Enable” and then click Apply. (ed. Varonis has a very solid IT security policy, because of course)
How to use PowerShell to Administer Group Policies
Many sysadmins are moving to PowerShell instead of the UI to manage group policies. Here are a few of the PowerShell grouppolicy cmdlets to get you started.
- New-GPO: This cmdlet creates a new unassigned GPO. You can pass a name, owner, domain, and more parameters to the new GPO.
- Get-GPOReport: This cmdlet returns all or the specified GPO(s) that exist in a domain in an XML or HTML file. Very useful for troubleshooting and documentation.
- Get-GPResultantSetOfPolicy: This cmdlet returns the entire Resultant Set of Policy (RsoP) for a user or computer or both and creates an XML file with the results. This is a great cmdlet to research issues with GPOs. You might think that a policy is set to a certain value, but that policy could be overwritten by another GPO, and the only way to figure that out is to know the actual values applied to a user or computer.
- Invoke-GPUpdate: This cmdlet allows you to refresh the GPOs on a computer, it’s the same as running gpupdate.exe. You can schedule the update to happen at a certain time on a remote computer with the cmdlet, which also means you can write a script to push out many refreshes if the need arises.
There are many more cmdlets in the ‘grouppolicy’ PowerShell object, but these four are especially useful to track down and resolve inheritance issues with GPOs.
PowerShell is one of a hacker’s favorite tools, and one of their favorite tricks is to enable the local administrator account that you have carefully disabled to gain control of a system for more infiltration or privilege escalation work.
It’s important to monitor Active Directory for any changes made to Group Policy – often these changes are the first signals in APT attacks, where hackers intend to be in your network for a while, and they want to remain hidden. Varonis monitors and correlates current activity against normalized behavior and advanced data security threat models to detect APT attacks, malware infections, brute-force attacks, including attempts to change GPOs.
Local Group Policy Editor Windows 10 Missing
Check out this PowerShell course by Adam Bertram for more PowerShell tips and tricks! It’s worth 3 CPE credits!
Group Policy Editor Windows 7
-->Applies To: Windows Server 2012 R2
Local Group Policy Editor is a Microsoft Management Console (MMC) snap-in that is used to configure and modify Group Policy settings within Group Policy Objects (GPOs).
Administrators need to be able to quickly modify Group Policy settings for multiple users and computers throughout a network environment. The Local Group Policy Editor provides administrators with a hierarchical tree structure for configuring Group Policy settings in GPOs. These GPOs can then be linked to sites, domains, and organizational units (OU) that contain computer or user objects.
Local Group Policy Editor consists of two main sections:
User Configuration Holds settings that are applied to users (at sign-in and during periodic background refresh),
Computer Configuration Holds settings that are applied to computers (at startup and during periodic background refresh).
These sections are further divided into the different types of policies that can be set, such as Administrative Templates, Security, and Folder Redirection.
To work efficiently, administrators need to have immediate access to information about the function and purpose of individual policy settings. For Administrative Templates policy settings, Local Group Policy Editor provides information about each policy setting directly in the web view of the console. This information shows operating system requirements, defines the policy setting, and includes any specific details about the effect of enabling or disabling the policy setting.
In addition, developers should be able to quickly and easily add Group Policy support to their software products. The Local Group Policy Editor is designed to be extensible. The easiest way for developers to extend Local Group Policy Editor for their applications is to write custom Administrative Template files that they can add to Local Group Policy Editor.
Use the Local Group Policy Editor
Download Local Group Policy Editor
The following procedures explain how to open the Local Group Policy Editor from the command line or as an MMC snap-in.
Local Group Policy Editor Windows 7
To open the Local Group Policy Editor from the command line
Local Group Policy Editor Windows Xp
- On the Start screen, click the Apps arrow. On the Apps screen, type gpedit.msc, and then press ENTER.
Where Is Local Group Policy Editor
To open the Local Group Policy Editor as a snap-in
On the Start screen, click the Apps arrow. On the Apps screen, type mmc, and then press ENTER.
On the File menu, click Add/Remove Snap-in.
In the Add or Remove Snap-ins dialog box, click Local Group Policy Editor, and then click Add.
In the Select Group Policy Object dialog box, click Browse.
Click This computer to edit the Local Group Policy Object, or click Another computer to edit the Local Group Policy Object for a different computer. Click Users to edit Administrator, Non-Administrator, or per-user Local Group Policy Objects.
Click Finish.
Note
If you want to save a Local Group Policy Editor console and choose which GPO opens in it from the command line:In the Select Group Policy Object dialog box, select the Allow the focus of the Group Policy Snap-in to be changed when launching from the command line check box.
